Business has grown to a point where users are no longer bound to traditional network boundaries. With shifts to cloud applications like Microsoft 365, it has become increasingly difficult for businesses to deliver fast, secure, and compliant connections to these applications. Vendors know this and have been working towards improving the technology offerings. Secure Access Service Edge (SASE) solutions have become the recent buzzword in technology for the exact reason that it was conceived to solve the above problems. SASE ensures that any connection originating from a user or device to any destination in the cloud is secure and meets the organization’s connectivity requirements.
However, some industries, like financial services, have unique situations where adopting solutions would also come with security risks associated with SaaS cloud delivered platforms. This is where iboss’ approach to SASE can help through its containerized based platform. Containerization allows iboss to deliver secure connectivity for users anywhere while maintaining a completely isolated and controlled network data path. A fully containerized architecture also has the benefit of synergizing well for hybrid deployments. It allows businesses to utilize their proxy and firewall security features within their private network while being able to leverage cloud-based service for their remote users or branches.
Below are a few features of iboss’ containerization architecture that can benefit those in the financial industry:
SaaS Network Security Service with Containerization

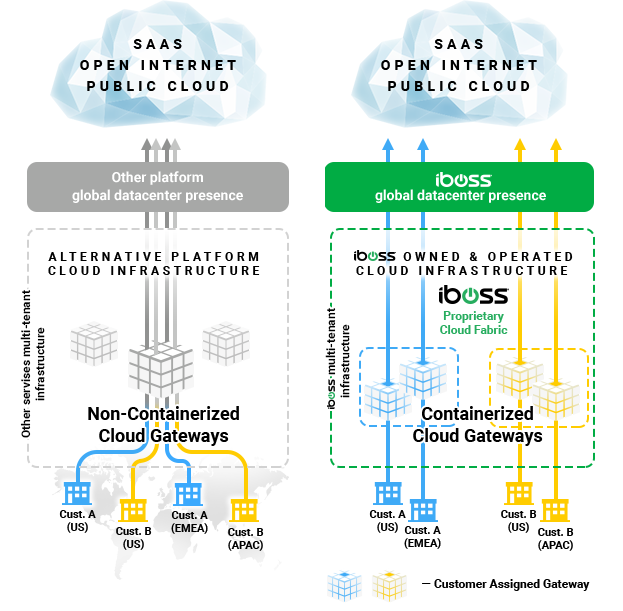
Containerization services like iboss allows network connections from devices and users to be processed within isolated containerized gateways which perform proxy and firewall functions. These gateways never process data for any other organizations and data is never mixed between different customers. The gateways can also be destroyed or created in seconds to provide horizontal scaling.
Better Security When Inspecting Traffic

The containerized cloud architecture that iboss provides also allows full isolation of data as it moves between the cloud and business users. This includes a full isolation of private keys required to decrypt the traffic of data during motion. The containerized cloud gateways isolate the private SSL decryption keys to ensure security and reduce risk. On the other hand, non- containerized cloud architecture has the private SSL decryption keys available to the gateways that decrypt the network traffic. This means that those gateways are decrypting and processing traffic for any organization that traverses that gateway. This can pose as a big security risk and can have serious implications for high-security industries like financial services.
Naturally Hybrid for Easy Deployment on Private Cloud

Containerized architecture allows not only for its use on cloud but can also be deployed within a company’s network. This includes running the gateways within an office or datacenter. With iboss, you can run containerized gateways on physical infrastructure within the business. Traffic can be subjected to a proxy or firewall directly within the organizations perimeter without ever sending it through the cloud gateways running within the service.
To learn more about the benefits of iboss solutions for finance or other industries, you can send us an email at marketing@www.ctlink.com.ph