In today’s hybrid environment, traditional enterprise architecture and security models are not up to standard when faced with the accompanying complex application-security requirements it brings. Companies are now shifting towards SaaS while maintaining their enterprise apps inside their datacenters. This is so that data is more accessible to their users as they collaborate through remote work solutions while still keeping their important applications within their network perimeter.
However, this approach makes the IT environment more complex and challenging when it comes to keeping it secure and easy to manage. Allowing non-compliant or unauthorized devices into your network in favor of BYOD for hybrid work opens up your network to more security risks. This is made evident in the past few years as more cyberattacks have been focused on users rather than businesses.
The common risks and challenges that businesses face can be summarized below:
- Cyberthreat Risks: Siloed point products cannot provide broad protection against cyberattacks
- Poor Experience: High latency to access applications when backhauling traffic thought the datacenter
- Complex Management: Multiple complex and hard-to-manage siloed technologies
- Too Much Work: Overwhelmed IT staff due to rapid usage and high dependency on VPN
- Slow Cloud Adoption: Complexity of transitioning to a cloud/multi-cloud architecture
- Expensive: Overspending on siloed, redundant, and disjointed security technology increases costs
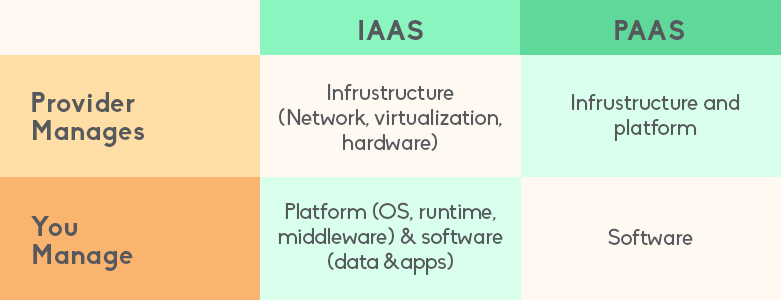
Citrix Secure Private Access

Knowing all of the above challenges, Citrix developed a Zero Trust Network Access (ZTNA) security solution that focused on solving them. Secure Private Access is a cloud delivered ZTNA service with capabilities such as adaptive authentication and adaptive access for web, SaaS, and TCP (e.g. SAP, Oracle) applications.
Traditional VPN solutions needed user devices to be managed to access the network which either used more resources then needed or had push back from users using BYOD. It also had the issues of allowing users more permissions or access than needed while having the additional downside of static access control policies. Citrix Secure Private Access on the other hand, allows your IT team a set of security controls to protect against BYOD and limiting the access of users to IT-sanctioned apps. Security policy options can also be applied to devices whether they are a company issued device or a BYO device.
Secure Private Access was not Citrix’s first foray into the ZTNA space as it was preceded by Secure Workspace Access. The main difference is that Citrix has updated its technologies to better handle the current business needs for a ZTNA solution. Below are key features that Secure Private Access has that Secure Workspace Access does not have:
ZTNA to all IT sanctioned applications
As stated above, Citrix Secure Private Access expands its ZTNA to applications running on TCP and UDP- based protocols. A feature not seen in the previous Citrix Workspace access which primarily focused on browser-based applications. This feature allows your IT to apply ZTNA to your business applications whether they are deployed on-premise or in the public cloud even if they are not going through Citrix Workspace.
Adaptive authentication, user risk score, SSO, and enhanced security
Citrix Secure Private Access can scan end-users devices and then give them a risk score. It then uses this as a basis before it allows any sessions to be established between your network and the device. Risk score is based on the user’s identity, geolocation, and the device-posture assessment. IT then can define how they want users to authenticate and authorize their access to the business application. This gives IT to control the actions users can take within the applications and can be implemented on all sanctioned applications, including Citrix Virtual Apps and Desktop service customers.
To learn more about the Citrix Secure Private Access or any other Citrix solution, you may contact us at marketing@www.ctlink.com.ph and we would be happy to set a meeting with you at your convenience!