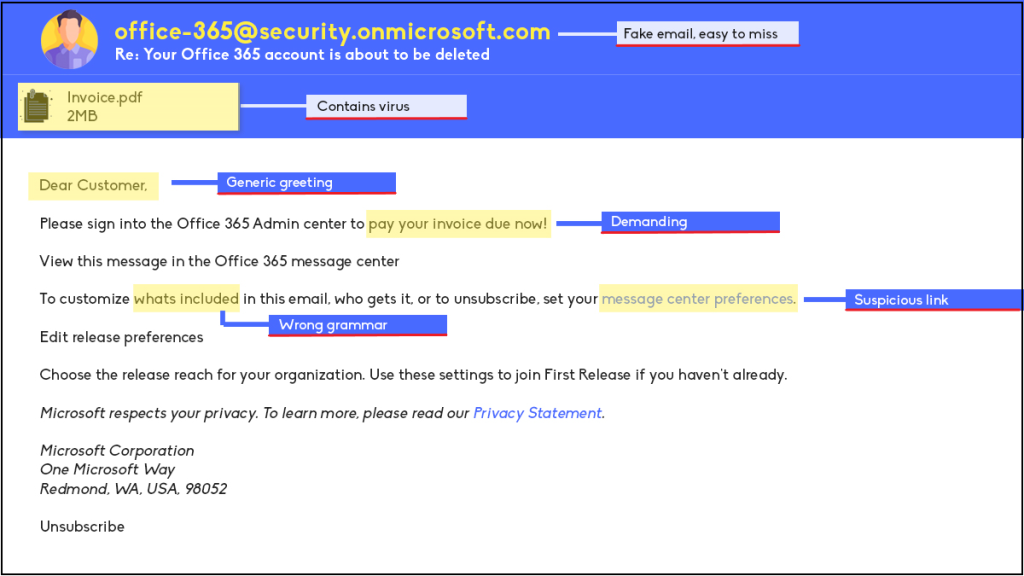
In the rapidly evolving digital landscape of the Philippines, where data is a precious resource, cloud security is more critical than ever. The adoption of hybrid cloud security in the Philippines has brought new challenges that many businesses are trying to solve. This is where Trend Micro Hybrid Cloud Security, Trend Vision One™, can help businesses address the new challenges through plethora of features perfect for the new hybrid landscape.
Trend Micro Hybrid Cloud Security Feature: Attack Surface Management
Trend Vision One™ – Cloud Attack Surface Risk Management is a tailor-made solution that delivers hybrid cloud telemetry correlation for fast detection and response with centralized risk visibility and benchmarking. It does this through the following key components:
Cloud Asset Visibility in the Philippines
To secure your cloud assets effectively, you first need a clear view of them. Trend Micro provides comprehensive visibility into your cloud assets, ensuring that no vulnerabilities go unnoticed in the unique Philippine digital landscape.
Mitigating Misconfigurations
Misconfigurations are a common entry point for cyber threats. Trend Micro helps you identify and rectify these issues, providing a strong defense against potential attacks in the Philippines.
Template Scanning for Philippine Cloud Environments
Scanning cloud templates is vital to building a secure cloud infrastructure. Trend Micro ensures that your cloud resources in the Philippines are constructed on a solid and secure foundation.
Compliance in the Philippines
Staying compliant with local and international regulations is essential. Trend Micro aids in compliance management, helping Philippine businesses reduce the risks associated with non-compliance.
Prioritizing Risks and Recommendations
In the diverse and dynamic digital landscape of the Philippines, not all risks are equal. Trend Micro helps you prioritize risks based on their severity and provides actionable recommendations for mitigation.
Addressing Threats and Vulnerabilities
The Philippines is not immune to cyber threats. Identifying and addressing threats and vulnerabilities is crucial, and Trend Micro’s hybrid cloud security solution is well-equipped to protect your assets.
Trend Micro Hybrid Cloud Security Feature: Cloud Protection
On-demand and runtime protection for your hybrid cloud is crucial for maintaining a secure digital landscape in the Philippines. Trend Micro offers a multi-layered approach to cloud protection.
Real-Time Integrity Monitoring
Ensure the integrity of your cloud workloads with real-time monitoring, ensuring that any unauthorized changes are promptly detected and addressed, even in the dynamic Philippine environment.
Application Control
Manage and control applications running in your cloud environment, preventing unauthorized or potentially harmful software from executing and maintaining the security of your digital assets.
Virtual Patching for Philippine Clouds
Virtual patching bridges the gap between identifying vulnerabilities and applying official patches. This proactive approach safeguards your systems and data, which is particularly crucial in the Philippine context.
Intrusion Prevention
Intrusion prevention systems work tirelessly to block malicious activities, ensuring that your cloud environment remains secure in the Philippine digital landscape.
Continuous Compliance
Maintaining compliance is an ongoing effort in the Philippines, and Trend Micro supports this by reducing your exposure to risks associated with non-compliance.
Guarding Against Malware
Malware poses a persistent threat in the digital world, and Trend Micro’s anti-malware solutions provide robust defense against these malicious agents, safeguarding businesses in the Philippines.
Trend Micro Hybrid Cloud Security Feature: Container Security
Containers have played a significant role in advancing digital innovation in the Philippines, but they come with their own set of security challenges. Trend Micro addresses these concerns comprehensively.
Vulnerability Management
Identifying vulnerabilities in containerized applications and addressing them is crucial for ensuring the security of your containers in the dynamic digital landscape of the Philippines.
Ransomware Protection
Ransomware attacks can be devastating for businesses. Trend Micro’s container security solutions guard against these threats, preventing data loss and financial damage in the Philippine context.
Image Scanning
Before deploying container images, it’s essential to scan them for potential threats. Trend Micro’s image scanning tools serve as the first line of defense, ensuring that your digital innovations remain secure in the Philippine landscape.
Drift Detection
Container environments are dynamic and ever-evolving in the Philippines. Trend Micro detects and responds to runtime threats and any suspicious activities that may arise in the rapidly changing digital landscape.
Cloud Detection and Response: Staying Ahead of Emerging Threats
In the Philippine context, staying ahead of emerging threats is essential to ensure the security of your digital assets. Telemetry enables cloud detection and response (CDR), extending the concept of Extended Detection and Response (XDR) to cloud provider and cloud-native technologies.
Telemetry Collection from Hybrid Workloads in the Philippines
For a comprehensive view of your digital assets in the Philippines, Trend Micro collects telemetry data from hybrid workloads, ensuring that your Security Operations Center (SOC) team has the insights they need to protect your digital landscape.
Unique XDR for Philippine Hybrid Environments
Trend Micro’s XDR solution is tailored to the unique needs of hybrid environments in the Philippines, covering servers, instances, and containers seamlessly.
Integration with Philippine Cloud Provider Logging Services
A broader view of your digital landscape in the Philippines is achieved by integrating with cloud provider logging services. Automation of remediation actions ensures a swift response to threats, which is crucial in the dynamic and evolving Philippine digital context.
Future-Proofing Cloud Security in the Philippines
Trend Micro Hybrid Cloud Security, with its Trend Vision One™ solution, is a trusted partner for securing digital assets in the dynamic and ever-evolving digital landscape of the Philippines. With robust attack surface management, real-time cloud protection, and advanced cloud detection and response capabilities, Trend Micro empowers businesses to safeguard their digital assets effectively.
To learn more about Trend Micro or learn more about hybrid cloud security, you may contact us at marketing@ctlink.com.ph to consult with us today!