Why is Email Security Service trending online?

Emailing has always been a key communication tool for businesses. It may even be the only way some people who are working remotely can communicate with clients and teammates. This has prompted businesses to improve their email infrastructure to improve user experience. However, email security service is something businesses should not forget.
Attacks are now targeting your users instead of your network perimeter. Although there is a silver lining to this. The growth of cyber-attacks in 2020 , we are seeing less ransomware attacks in 2021. This is not due to attackers using it less, security vendors have adapted to the more commonly used attacks. Though keep in mind that many cyber criminals have started to concentrate their efforts on targeted attacks.
There are multiple steps businesses must take to ensure proper protection from these threats. The most important step is to train your staff on how to spot and respond to BEC attacks. However, no matter how well trained your users are, human error will occur. One wrong click can put your business at risk. Attacks also now mimic writing styles of those who work in the organization to make it even more convincing. This is where an Email Security solution can help.
CT Link Systems, Inc. can help ease your worries with services aimed to make email security implementation easier. We work with your team to find the best security policies for your solution while maintaining a seamless experience. We accomplish our email security service through the following framework below:
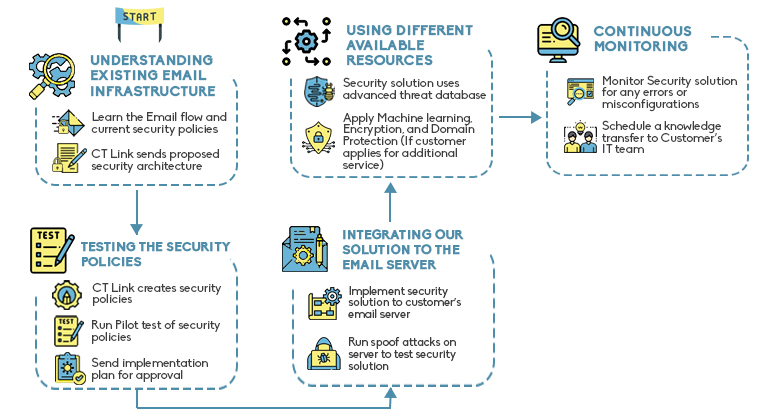

Understanding Existing Email Infrastructure
We first take a look at your current email infrastructure. Learning how you email flow works is essential in making a better security infrastructure. We send our proposed security architecture design to your team after this step.

Testing the Security Policies
We run a pilot test for the security policies before implementation. This is to ensure we keep errors and misconfigurations at a minimum during the live application.

Integrating Our Solution to the Email Server
Once live, we do a series of spoof attacks to test the security solution. We do this to make sure that the security solution is running as intended.
Using Different available resources
The security solution makes use of a continuously updated threat database. Making use of this database ensures that the solution stays relevant against emerging threats. Our solution also has the option for encryption and machine learning. This is to help lessen data loss in your business.
Another thing to consider is the risk of fake domains. Social engineered attacks are becoming more common and harder to spot. With our Email Domain Protection, you can better protect your users from these attacks.

Continuous Monitoring
The last step is to continuously monitor the live solution. Once everything is running as planned, we start the knowledge transfer to your team.
