With the rising number of cyber threats and strict data protection laws like the GDPR, businesses need to make securing their email communications a top priority. Let’s dive in on what the GDPR email security requirements are and what it means for Philippines businesses.
Understanding GDPR and Email Security

The General Data Protection Regulation (GDPR) is a powerful data protection law established by the European Union in 2018. Its main goal is to protect personal data and give individuals more control over how their information is used. The regulation includes key rules, such as the right for individuals to access, correct, or delete their data, and requires organizations to implement proper security measures to safeguard this information.
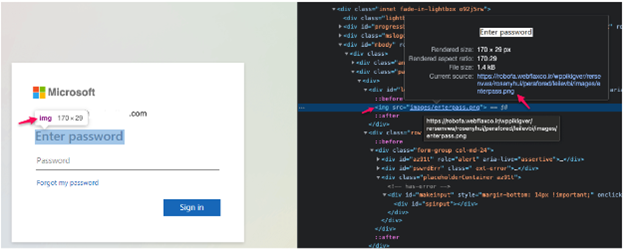
Email security plays a vital role in meeting GDPR requirements, especially when it comes to defending against sophisticated threats beyond common phishing and spam. Today, businesses must stay alert to dangers like Business Email Compromise (BEC) and QR Code Phishing (Quishing). BEC involves attackers gaining access to a company’s email system to impersonate employees or trusted partners, often leading to severe financial losses. Quishing, on the other hand, uses QR codes to lure users to malicious websites, which is becoming a bigger threat as QR codes are used more frequently.
Key technologies that bolster email security include:
Spam Filters: These tools are crucial for screening incoming emails and identifying harmful content. Using pattern recognition and machine learning, spam filters can block not only traditional spam but also more advanced phishing attempts.
Email Encryption: This ensures that only the intended recipients can read the emails. Technologies like S/MIME and PGP encrypt emails, protecting sensitive data during transmission and preventing unauthorized access.
Secure Email Gateways: Acting as the first line of defense, these gateways analyze and filter all email traffic. They use multiple layers of security, including malware detection, data loss prevention, and encryption, to guard against both known and emerging threats.
Data Loss Prevention (DLP): DLP tools monitor email content to prevent the accidental or intentional sharing of sensitive information. By enforcing data protection policies, DLP ensures compliance with GDPR and other data protection regulations.
Credential Stuffing and Session Hijacking Prevention: As attackers increasingly use stolen credentials from unrelated breaches to gain unauthorized access, businesses need to adopt measures to detect and block credential stuffing. Additionally, securing session management practices is essential to prevent session hijacking, where attackers take over a user’s session to impersonate them.
Implementing GDPR-Compliant Email Security Measures

The GDPR requires organizations to take strong security measures to protect personal data, making email security a key priority. Technologies like email encryption and secure gateways are crucial for keeping communications private and safe from unauthorized access. Advanced email security tools not only help prevent breaches but also allow businesses to quickly respond to and report any incidents, helping them stay compliant with GDPR.
For businesses in the Philippines, these measures are especially important due to the Data Privacy Act of 2012 (DPA), which shares many of the same requirements as GDPR. By adopting GDPR-compliant email security practices, Filipino businesses can avoid penalties when handling data from EU citizens, enhance their reputation, and build trust with international partners. Using technologies like spam filters, secure email gateways, and DLP systems not only strengthens email security but also ensures compliance with both GDPR and DPA standards.
To learn more about Email Security solutions or other solutions for the GDPR or DPA, contact us at marketing@ctlink.com.ph to set a meeting with us today!